Website Vulnerability Scanning Using BackTrack
Scan Website For Vulnerabilities Using BackTrack - Uniscan
Hello CHC members we gonna scan for vulnerabilities in a website, or all the websites in the server.
In this tutorial I will use a program in BackTrack called UniScan. it's very easy to use, but very good in scanning.First of all, open your terminal and type this command: cd /pentest/web/uniscan && ./uniscan.pl
Something like this will be printed on your terminal. Now all we have to do is follow the instructions. First of all we need a target to scan, I've chose one already and I will use it in my pictures. To start the scan, first you have to check the options which you want to use in your scan.
# HOW TO USE OPTIONS: Check the letter beside your option, and include it after the URL like this:
./uniscan.pl -u http://www.website.com/ -b -q -d -w or put them all together.
./uniscan.pl -u http://www.website.com/ -bqdw .This will start your scan with all the different options you included.
NOTE:- NEVER FORGET THE FORWARD SLASH AT THE END OF THE LINK IN THE END!!
Now the scan will start, and the terminal will look something like this:
This scan will scan for vulnerabilities like SQL-i / LFI / RFI and so on. It also searches for Webshells, backdoors, PHP info disclosure, Emails, and much more.
Here are some examples:
PHP.info() disclosure:
External Links/Hosts:
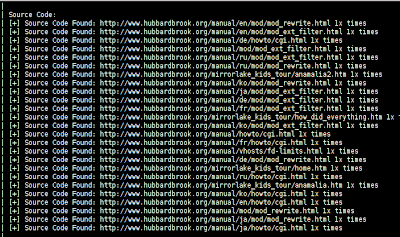
Source Code disclosure:
Dynamic Scan, Vulnerability Identification:
This program can also get all the sites in a server, and then you will be able to scan all of them. To do that, run this command:
./uniscan.pl -i "ip:127.0.0.1"
Change 127.0.0.1 to your target server. All the websites will be stored in "sites.txt" in the same directory.
Now to scan those sites in the list, run this command:
./uniscan.pl -f sites.txt -bqwd
You can change the options to whatever you want.






nice man
ReplyDeleteThis comment has been removed by the author.
DeleteThank you so much dude, been looking for something like this! Keep up the good work! :D
ReplyDeleteThis comment has been removed by the author.
DeleteAwesome buddy... :D
ReplyDelete