Introduction to Metasploit
Metasploit - Overview
What is metasploit?
Metasploit as described by its developers is :"A collaboration between the open source community and Rapid7, Metasploit software helps
Metasploit editions range from a free edition to professional enterprise editions, all based on the Metasploit Framework, an open source software development kit with the world's largest, public collection of quality-assured
There are many Metasploit editions: metasploit community, metasploit express, metasploit pro & metasploit framework. There are also different interfaces for this tool: msfconsole:
msfcli:
and msf gui which is the graphiical
You have to know also that there is no perfect interface for metasploit, each one has its pros & cons.
Architecture:
Terminology:
1. Exploits: exploits are security flaw that allow a pentester to attack targets.
2. Payloads: Allow attacker to generate shellcodes, executable files, and simply specify the work of the payload.
3. Auxiliaries: integrated applications like sniffers, keyloggers ..
4. Meterpreter: An injected payload into a system process.
5. Encoders: Used to allow the modification of original exploit codes so that to shun antivirus detection software.
Basic commands:
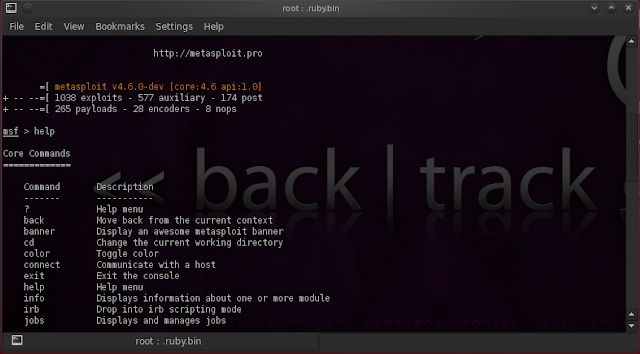
1. Help: Displays all the metasploit commands:
2. Search: You can use if you are not sure about the exact name of a certain exploit. If you want to look for an "smb" exploit for example you type: search smb:
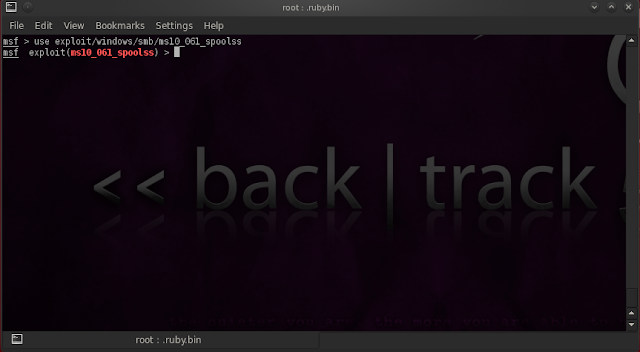
3. use: Used to select a particular exploit:
4. info: Used to provide information about the selected exploit:
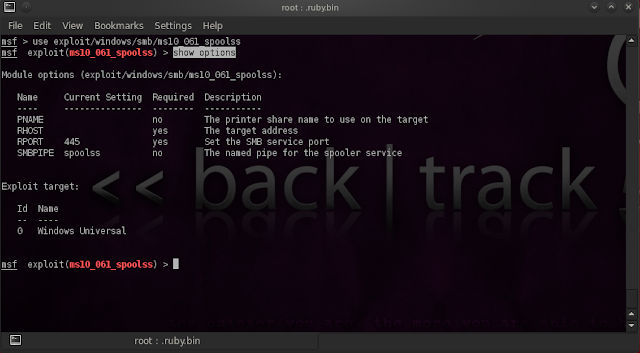
5. show options: Used to show all options of a given exploit:
6. show: Used to display all the available payloads, encoders, and nops arelated to a given exploit:
7. set: Used to configure a given exploit:
Chennai Hackers Connect hopes that this article was useful to you.











0 comments: